
WAF: Why Your Web App Project Needs Protection
Protecting your project is integral to ensuring a problem-free journey from its inception to completion. And with thousands of attacks occurring every minute globally, you cannot afford to remain unprotected.
Web App-Targeted Attacks
Every day, our DevSecOps team detects hundreds of suspicious requests from unknown users attempting to exploit vulnerabilities. Missing even one of these attacks could compromise our infrastructure and put our clients' data at serious risk — a risk that is simply unacceptable to Connect-i.
This is why our infrastructure detects and fends off such network-based threats with advanced security measures, including firewalls, which are crucial for monitoring and controlling incoming and outgoing network traffic.
But how do we protect our website from more sophisticated, application-specific attacks like XSS, SQL injections, DDoS, and so on? This is where a Web Application Firewall (WAF) comes into play. Using a WAF, we add an essential layer of protection that goes beyond the capabilities of traditional firewalls, ensuring that our website remains secure from targeted attacks.
What Is a Web Application Firewall?
A Web Application Firewall (WAF) is a crucial security measure for websites, mobile apps, and APIs. A WAF filters, monitors, and blocks HTTP requests and data packets going to and from web applications, shielding them from potential threats.
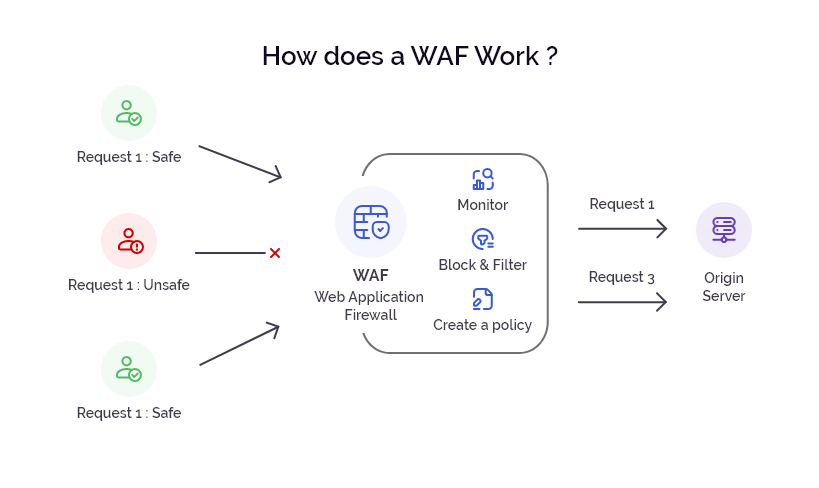
WAFs are specifically designed to identify and counteract common web traffic security vulnerabilities, making them indispensable for online enterprises that must safeguard sensitive information from unauthorized access.
These firewalls can be implemented as network-based, host-based, or cloud-based solutions, offering insight into application data at the HTTP application layer.
How to Use a WAF?
While regular, network-level firewalls filter traffic based on IP addresses, ports, and protocols, protecting the network perimeter by blocking or allowing traffic based on these criteria, WAFs can manage more granular application-level rules.
They filter, analyze logs, and block access based on IP addresses, IP address ranges, Autonomous System Numbers (ASNs), or countries.
Moreover, it's possible to customize rules to block users based on their behavior. For instance, your Drupal-based website receives a request to access this page:
https://example.com/wp-content/plugins/wpcargo/includes/barcode.php.
The "wp-content" in the address indicates a WordPress site, whereas your product is based on Drupal. This suggests the request might be from a crawler targeting WordPress sites.
Such automated crawlers actively probe for the site's defenses, misconfigurations, or security gaps through your site's responses to unusual requests. Their presence is a red flag, even if the website is not running WordPress, and it's prudent to block such requests to avoid unnecessary traffic and potential security risks. To address this, we can set a WAF rule to block any requests containing "wp-content" altogether.
Defend Your Web Applications with Connect-i
Integrating Web Application Firewalls into client systems is becoming increasingly prevalent as companies grow aware of the severe consequences of hacking incidents and recognize that traditional security measures alone are not enough to protect against sophisticated web-based attacks.
A WAF offers an additional layer of defense by filtering and monitoring HTTP requests, ensuring that potential threats are caught and mitigated before they can cause harm.
If you're concerned about cybersecurity and want to stay ahead of emerging threats, reach out to us to learn how Connect-i can help safeguard your systems with cutting-edge WAF technology. We provide tailored solutions to enhance your security posture so that you can have greater peace of mind and focus on your core business activities.


