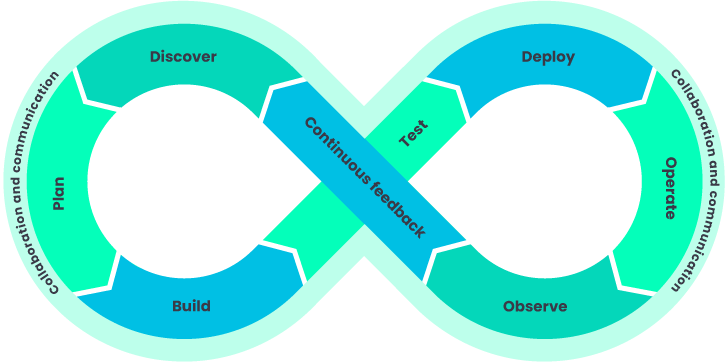
DevOps breaks down the silos between software development and IT operations, transforming the latter into an active driver of software delivery efficiency.
This approach encompasses many complex practices, including automation, continuous integration and delivery (CI/CD), infrastructure as code, comprehensive monitoring, adopting a microservices architecture, fostering a collaborative culture, establishing robust feedback loops, enforcing stringent security measures, and ensuring scalability and resilience.
Implementing these practices to work harmoniously demands significant expertise.