The Seven Layers of Cybersecurity: A Comprehensive Framework for Protecting Information and Systems
Cybersecurity is an increasingly critical and complex aspect of the digital world. With the rise of sophisticated cyber threats, organizations and individuals must take proactive steps to safeguard their systems and data from unauthorized access, damage, or theft.
This article will explore the concept of the "seven layers of cybersecurity," a comprehensive framework that provides a structured approach to protecting information and systems from various cyber risks. Additionally, we will discuss how Connect-i can help enhance security through penetration testing services, allowing you to identify and address vulnerabilities before malicious actors exploit them.

Understanding the OSI Model
Before delving into the seven layers of cybersecurity, it is essential to understand the Open Systems Interconnection (OSI) model. Developed by the International Organization for Standardization (ISO), the OSI model serves as a conceptual framework for communication between computer systems over a network using standard protocols.
This model divides the communication process into seven abstraction layers, each with its specific function and responsibility. By providing a common language and framework, the OSI model ensures interoperability and compatibility among different systems and networks, making it a widely used and referenced model in the field of information technology.
The Seven Layers of Cybersecurity
Cybersecurity comprises a set of protective measures that can be applied at different levels or domains to secure information and systems against various cyber threats. Among the different frameworks and models available, the "seven layers of cybersecurity" based on the OSI model is one of the most common.
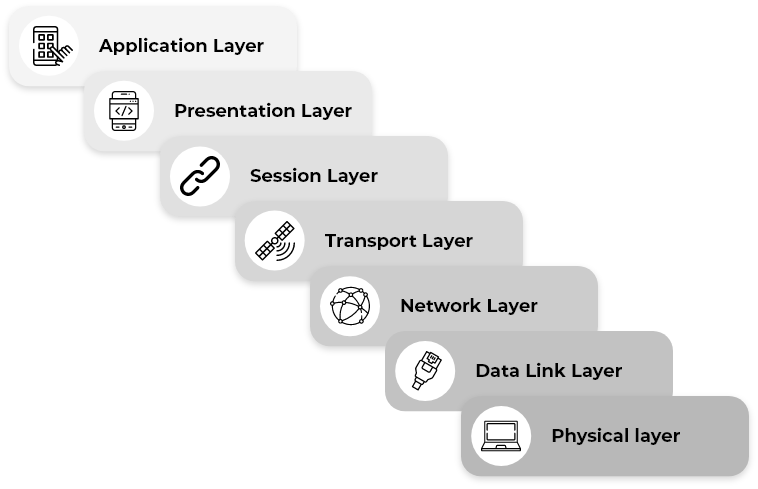
Each layer represents a distinct aspect of security. Let's examine them closely:
Physical Layer
The physical layer focuses on securing the physical components of a system or network, such as servers, routers, switches, and cables. Measures at this layer include controlling physical access, installing surveillance systems, and preventing theft or damage.
Data Link Layer
The data link layer ensures the security of data transmissions between neighboring network nodes. Techniques such as encryption, access control, and data validation are employed to maintain data integrity and confidentiality during transmission.
Network Layer
The network layer deals with securing network communications and logical addressing. Firewalls, intrusion detection systems (IDS), and virtual private networks (VPNs) are utilized to protect against unauthorized access and network-based attacks and ensure secure routing.
Transport Layer
The transport layer ensures reliable and secure data transfer between end systems. Encryption protocols like Transport Layer Security (TLS) and Secure Sockets Layer (SSL) are commonly implemented at this layer to guarantee data integrity, confidentiality, and authenticity.
Session Layer
The session layer manages and maintains communication sessions between applications. It establishes, maintains, and terminates connections between systems securely. Measures such as session authentication, encryption, and management prevent unauthorized access and session hijacking.
Presentation Layer
The presentation layer focuses on the interpretation and formatting of data to ensure its understandability by the receiving system. Techniques like encryption, data compression, and data transformation are employed at this layer to protect against data manipulation and unauthorized access.
Application Layer
The application layer, closest to the end-user, encompasses the actual applications and services. It is responsible for securing the applications themselves through robust authentication mechanisms, access controls, and secure coding practices. These measures defend against application-level attacks such as SQL injection, cross-site scripting (XSS), and other vulnerabilities.
It's important to note that while the seven-layer model provides a helpful framework, the implementation of security measures may vary depending on specific requirements, industry standards, and the nature of the systems or networks being protected. Modern cybersecurity approaches often incorporate additional layers and technologies to effectively address emerging threats and challenges.
Enhancing Security with Penetration Testing
In addition to the seven layers of cybersecurity, Connect-i offers penetration testing services as a proactive measure to identify vulnerabilities and assess the effectiveness of existing security measures. Penetration testing involves authorized simulated attacks on systems, networks, or applications to uncover potential weaknesses that malicious actors could exploit.
As cyber threats evolve, a structured approach to cybersecurity is crucial for protecting information and systems. The seven layers of cybersecurity based on the OSI model provide a comprehensive framework for implementing security measures at different levels. Connect-i's penetration testing services further enhance security by identifying vulnerabilities and enabling proactive risk mitigation.
By adopting these practices, organizations and individuals can fortify their defenses and ensure their critical assets' integrity, confidentiality, and availability in the face of an increasingly hostile digital landscape.